Table of Contents
ToggleLyzr Agent Studio enables developers to build, orchestrate, and deploy AI agents that execute tasks across APIs and applications. With the new Custom Tool integration via ACI.dev, developers can now extend these capabilities by integrating any external or internal system into their agents.
This update introduces a flexible framework for connecting APIs through API Key, OAuth, or No Authentication methods all defined through JSON configurations.
Each integration is secure by design, allowing developers to manage credentials, tokens, and data governance directly within their preferred environment.
The Custom Tool framework gives developers full control over how agents interact with third-party or in-house systems, without depending on predefined connectors or shared authentication models.
Building Secure Integrations Inside Agent Studio
Most agent frameworks rely on prebuilt connectors that manage authentication centrally. While convenient, this approach often limits flexibility and introduces security trade-offs, especially when dealing with sensitive or internal systems.
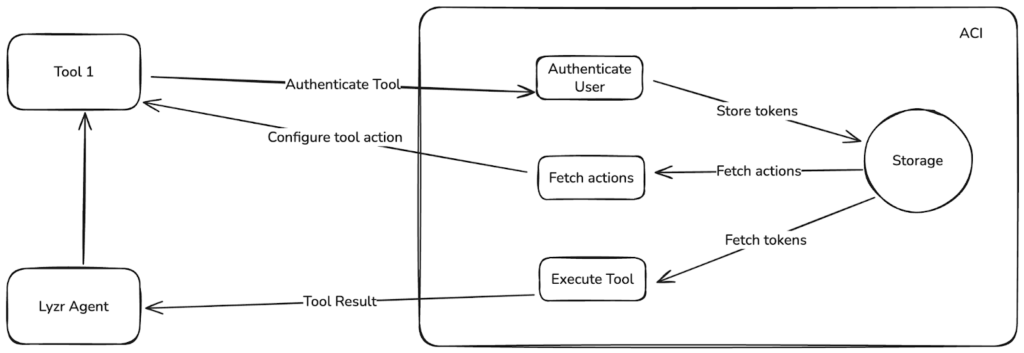
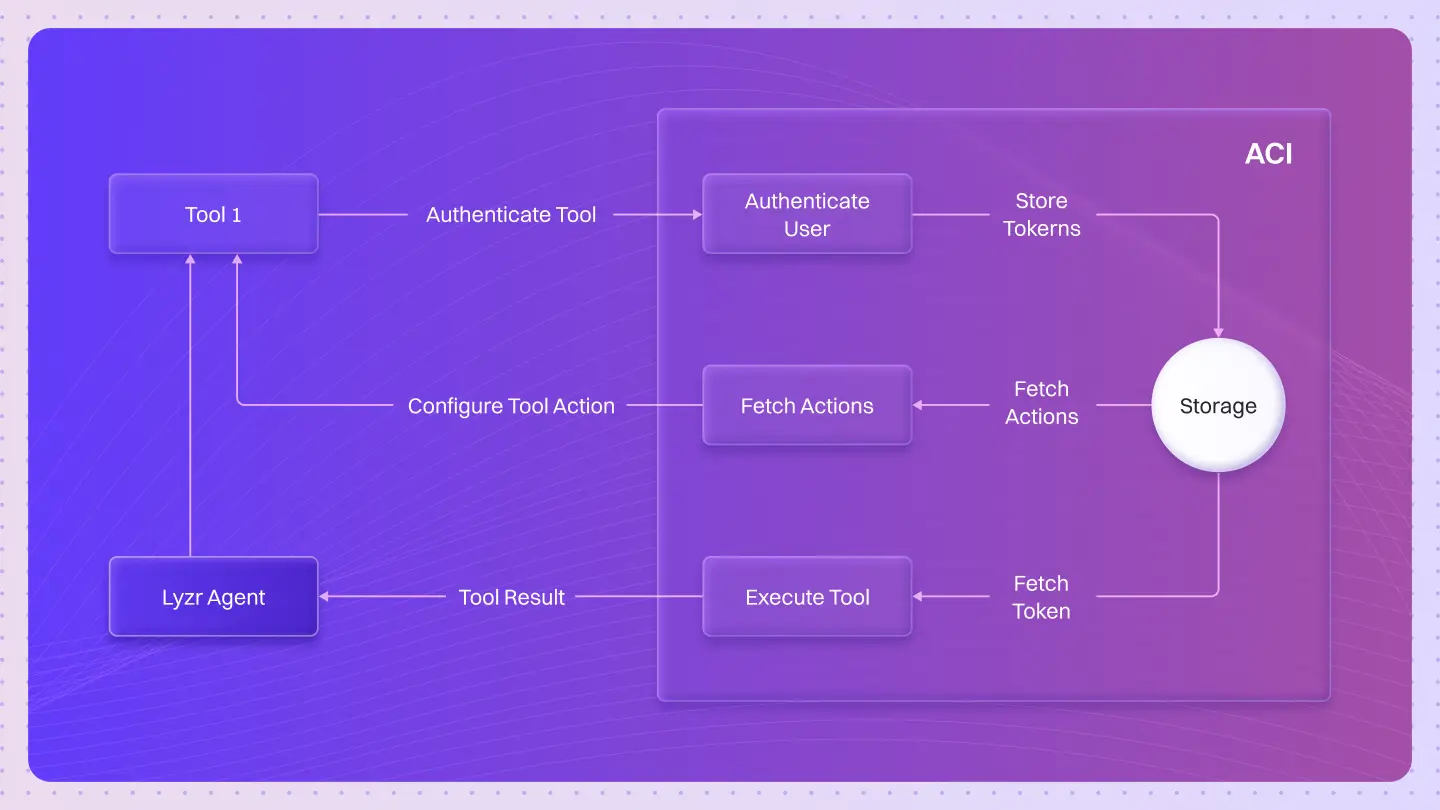
Agent Studio takes a different approach. Through ACI.dev, developers can define and manage how agents connect to external APIs while maintaining full visibility into data flow, access, and credential handling.
This architecture supports both SaaS and on-premise deployments:
- In SaaS mode, all access keys and refresh tokens are encrypted and stored within Lyzr’s infrastructure.
- In on-premise environments, the same setup can run entirely inside the client’s infrastructure, keeping all data and credentials under their control.
This model ensures that integrations can scale securely, from lightweight API connections to enterprise-grade systems, without exposing sensitive information outside authorized environments.
How the Custom Tool Framework Works
The Custom Tool framework in Agent Studio lets developers connect external or internal systems through a controlled and secure setup. It focuses on three core aspects: credential handling, authentication control, and tool creation flexibility.
1. Credential Handling
Developers can decide how and where their credentials are stored:
| Deployment Type | Storage Model | Control |
| SaaS | Credentials are encrypted and stored within Lyzr’s managed infrastructure | Lyzr manages encryption and access isolation |
| On-Premise | The entire setup runs within the client’s infrastructure | Full ownership and control remain with the client |
This model ensures security and compliance regardless of how Agent Studio is deployed.
2. Authentication Control
Agent Studio supports client-owned OAuth applications, giving organizations complete control over authentication and data permissions.
Instead of relying on Lyzr’s default OAuth apps, clients can register their own.
This approach allows:
- Independent management of access scopes and tokens
- Full alignment with internal governance policies
- Secure token handling without exposing credentials externally
While Lyzr securely stores tokens required for runtime, all data access remains governed by the client.
3. Tool Creation and Integration
Developers can define and register custom tools using simple JSON configurations. Each tool can authenticate using one of three supported methods:
| Authentication Type | Description |
| API Key | Ideal for static authentication models with header-based API keys |
| OAuth | Supports dynamic token-based authentication with automatic refresh |
| No Authentication | For public or internal endpoints that don’t require credentials |
Custom tools can also include token and refresh URLs. Agent Studio then handles refresh cycles and background authentication automatically.
This setup allows agents to integrate directly with internal APIs, SaaS services, or private systems while maintaining complete control over how authentication and data flow are managed
Adding a Custom Tool in Agent Studio
Agent Studio allows developers to register and configure custom tools directly through JSON definitions. Each integration consists of two components:
| Component | Purpose |
| App JSON | Defines the tool’s metadata, authentication type, and provider information |
| Function JSON | Defines the specific actions or functions that the agent can perform using that tool |
This modular design makes it simple to extend agent functionality without altering the agent’s core logic. Once a tool is defined, it becomes available for any agent within the workspace.
Below are two example configurations that demonstrate different authentication methods.
Example 1: Brave Search (API Key Authentication)
This configuration allows agents to access Brave Search’s public API using a static API key.
{
"name": "BRAVE_SEARCH",
"display_name": "Brave Search",
"provider": "Brave Software, Inc.",
"version": "1.0.0",
"description": "Brave Search API allows querying web, image, and news search results.",
"security_schemes": {
"api_key": {
"location": "header",
"name": "X-API-Key"
}
}
}Once this tool is registered, agents can call Brave Search endpoints as part of their workflow by including the function definitions within the Function JSON.
Example 2: Gmail (OAuth2 Authentication)
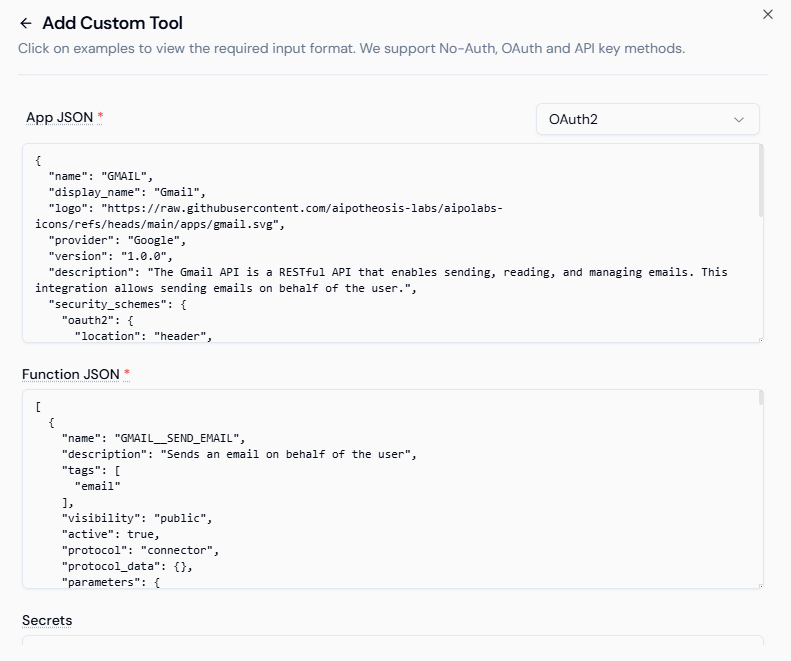
This setup connects Gmail through OAuth2. It enables agents to send and manage emails securely on behalf of users.
{
"name": "GMAIL",
"display_name": "Gmail",
"provider": "Google",
"version": "1.0.0",
"description": "Gmail API enables sending and managing emails securely.",
"security_schemes": {
"oauth2": {
"location": "header",
"authorization_url": "https://accounts.google.com/o/oauth2/auth",
"token_url": "https://oauth2.googleapis.com/token"
}
}
}Once added, Agent Studio handles the OAuth token exchange and refresh cycles automatically. Developers only need to specify the client credentials and redirect URLs during setup.
How Agent Studio Differs from Composio
Agent Studio and Composio both connect agents to external services, but their structure and intent differ. Agent Studio focuses on enterprise control and customization, while Composio is more suited for quick API access and testing.
1. Integration Approach
- Agent Studio lets developers define integrations directly within the Studio using JSON schemas.
- Composio relies on prebuilt APIs accessed through its SDK.
2. Authentication & Control
- Agent Studio supports both API Key and OAuth2 authentication in a declarative way, keeping credentials under enterprise control.
- Composio manages authentication through its own platform, which can limit flexibility in enterprise environments.
3. Hosting and Data Flow
| Function | Agent Studio | Composio |
| Hosting | Runs within Lyzr’s orchestration layer | Proxies requests via Composio’s servers |
| Data Flow | Stays inside enterprise setup | Flows through Composio infrastructure |
4. Customization Depth
Agent Studio supports custom function definitions for any service, making it suitable for internal workflows and secure enterprise systems.
Composio works better for integrating public APIs during early prototyping.
Wrapping Up
Agent Studio’s integration with ACI.dev marks a major step toward giving enterprises complete data control and customization flexibility. From secure key management to organization-specific OAuth setups and per-user tool configurations, every layer is designed to maintain privacy without compromising ease of integration.
The Custom Tool Framework expands this capability even further, enabling teams to define, authenticate, and manage their own tools natively within Agent Studio. Whether hosted in the cloud or deployed on-premise, the control remains entirely in the client’s hands.
Agent Studio simplifies the process of bringing external systems, APIs, and internal workflows into one unified agent environment, the privacy, compliance, and reliability built in from the start.
Start building with Agent Studio today.
Book A Demo: Click Here
Join our Slack: Click Here
Link to our GitHub: Click Here