Table of Contents
ToggleAs enterprises evolve from experimental AI pilots to fully autonomous, production-grade deployments, security and governance emerge as non-negotiable priorities. Agentic AI, where autonomous systems make independent decisions, access sensitive data, and interact with mission-critical infrastructure, introduces both opportunity and risk.
Organizations deploying these systems must address key questions:
- How can autonomous agents be trusted with enterprise data?
- How can isolation and control be enforced at scale?
- How can compliance be automated without slowing innovation?
This is where Lyzr’s AWS-native agent architecture stands out. Built on foundational AWS security and compliance features—and informed by the zero-trust principles seen in Zscaler and the isolation practices adopted by DeepBrain AI—Lyzr ensures every autonomous agent operates securely, transparently, and responsibly.
Enterprise-Grade Security: Built-In from Day One
Security within agentic systems cannot be an afterthought. Lyzr embeds security into the architecture itself, leveraging AWS’s layered defense model to protect data, execution, and communication channels across every stage of the agent lifecycle.
1. IAM Role-Based Access Control
Each agent within Lyzr operates under a dedicated IAM role with least-privilege permissions. This ensures agents only access the resources explicitly defined by enterprise policy—no shared credentials, no excessive privileges.
This principle directly aligns with Zscaler’s zero-trust architecture, where identity is the new perimeter and every request must be authenticated and authorized.
2. Continuous Threat Detection with Amazon GuardDuty
Agents and their network flows are continuously monitored using Amazon GuardDuty. The service uses ML-based anomaly detection to identify suspicious behavior, such as unusual API calls or unauthorized data transfers, triggering real-time alerts for remediation.
3. KMS-Backed Encryption
All data in motion and at rest is encrypted using AWS Key Management Service (KMS). This includes internal agent-to-agent messages, stored prompts, knowledge embeddings, and logs—ensuring no sensitive information is exposed during computation or transmission.
4. Secure Network Boundaries with VPC Segmentation
Agents are deployed within isolated VPCs (Virtual Private Clouds). Each VPC can be configured with private subnets, restricted network access, and security group policies—ensuring only trusted endpoints can communicate with agent environments.
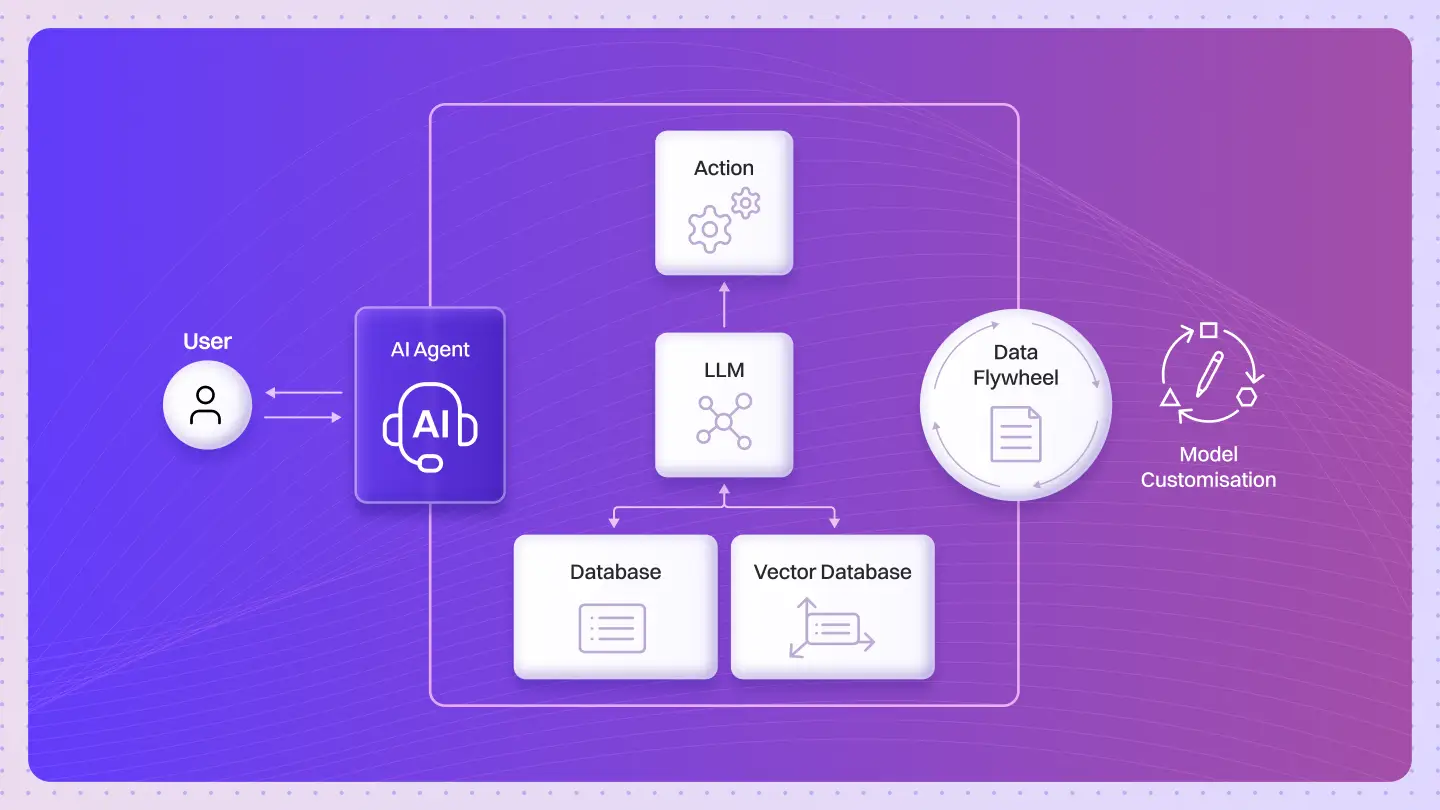
Agent Isolation & Orchestration
Autonomous agents thrive on collaboration, but collaboration must not come at the cost of security. Lyzr’s multi-agent design isolates workloads to minimize blast radius and prevent cross-agent interference.
1. Modular Deployment: Serverless and Containerized
Agents can be deployed as serverless AWS Lambda functions or containerized microservices on AWS Fargate or ECS. This flexibility enables organizations to select the execution mode best suited for performance and security needs.
2. Sandbox Execution Environments
Each agent runs within a sandboxed environment that isolates compute, memory, and storage. This prevents any lateral movement or data leakage between agents—a design pattern similar to DeepBrain AI’s isolation standards for safe model orchestration.
3. Secure Multi-Agent Communication
Agent-to-agent communication is managed through AWS API Gateway and event-driven services like Amazon EventBridge. All messages pass through authenticated, encrypted channels, ensuring that no direct or unmonitored communication occurs between agents.
4. Monitoring & Observability
Lyzr integrates natively with Amazon CloudWatch and AWS X-Ray, providing visibility into every agent’s activity, latency, and error patterns. Suspicious activities, such as repeated unauthorized API calls, are flagged for review by the security team.
Agent Isolation vs. Traditional AI Systems
| Feature | Traditional AI Systems | Lyzr Agentic AI on AWS |
|---|---|---|
| Execution Model | Monolithic or shared processes | Independent Lambda or container instances |
| Security Scope | Shared credentials across components | Individual IAM roles per agent |
| Communication | Direct peer-to-peer or API calls | Encrypted, authenticated API Gateway |
| Monitoring | Centralized, limited observability | CloudWatch & X-Ray with agent-level traceability |
| Threat Containment | High blast radius | Isolated VPCs and sandboxed execution |
Compliance & Responsible AI
Regulatory scrutiny is increasing across all AI deployments—especially in sectors like banking, healthcare, and government. Lyzr simplifies compliance through automation and transparency while maintaining adherence to AWS’s shared responsibility model.
1. Automated Compliance with CloudFormation Templates
Enterprises can deploy agents using pre-approved AWS CloudFormation templates, embedding organization-specific compliance configurations such as encryption standards, retention policies, and audit logging.
2. Continuous Model Monitoring
Each agent’s output is continuously evaluated for bias, accuracy, and consistency. Lyzr’s built-in model monitors integrate with CloudWatch and third-party analytics tools, ensuring compliance with GDPR, SOC 2, and ISO 27001 frameworks.
3. Human-in-the-Loop Validation
Lyzr’s Agent Studio includes human-in-the-loop checkpoints, allowing teams to review, approve, or override agent decisions when necessary. This ensures accountability, transparency, and responsible deployment.
The Lyzr Difference on AWS
While most frameworks retrofit security controls after deployment, Lyzr’s foundation is natively secure by design. Every agent runs within AWS’s zero-trust infrastructure, benefiting from a defense-in-depth strategy that extends from identity to execution.
Differentiators that Set Lyzr Apart
- AWS-Native Security Fabric: End-to-end protection through IAM, GuardDuty, VPC, and KMS
- Zero-Trust Agent Collaboration: Borrowing from Zscaler’s principles, no implicit trust, every interaction authenticated
- Modular Isolation Model: DeepBrain-inspired architecture ensures sandboxed micro-environments for each agent
- Continuous Compliance Automation: Built-in checks and logs aligned with enterprise audit workflows
- Scalable Governance: Centralized visibility and policy enforcement for multi-agent ecosystems
Real-World Use Cases
- Financial Services: Agents executing trade analysis and reporting within SOC2-compliant, encrypted environments
- Healthcare: Agents managing patient workflows under HIPAA constraints with strict data segregation
- Customer Operations: Agents interacting with sensitive CRM systems through secure, tokenized API access
Building Trustworthy Autonomous Solutions at Scale
Agentic AI will define the next phase of enterprise automation, but only if trust is built into the foundation. With Lyzr and AWS, enterprises gain a platform that is not only intelligent but also defensible, observable, and compliant by design.
From identity-first access to zero-trust collaboration, Lyzr turns the challenge of securing autonomous agents into a scalable framework for innovation—enabling organizations to deploy confidently in regulated and high-stakes environments.
Wrapping Up
As AI agents grow more autonomous, security and governance must evolve in parallel. Lyzr’s AWS-native approach, combining zero-trust principles, agent isolation, and compliance automation, offers a blueprint for enterprises aiming to balance agility with assurance.
Whether building a customer-facing assistant or orchestrating cross-departmental agents, trust begins at the infrastructure level. With Lyzr on AWS, that trust is not just configured, it is architected.
Book a demo to see how
Book A Demo: Click Here
Join our Slack: Click Here
Link to our GitHub: Click Here